Regulators and Threat-led Penetration Testing

I will say up front in this article that we appreciate that as a supplier in the field of cybersecurity our thoughts can hardly be claimed to be unbiased – we benefit from regulators enforcing Threat-Led Penetration Tests (TLPT, otherwise known as red teaming). In previous blogs we have mentioned that security is viewed as […]
UK Government Proposes Ban on Public Sector Ransomware Payments

On 22nd July 2025, the UK Government announced a significant legislative proposal aimed at reducing the incentive for ransomware attacks. Under the proposed law, public sector bodies and operators of Critical National Infrastructure (CNI) — including schools, local councils, the NHS, utilities, and data centres — would be prohibited from paying ransoms to cybercriminals. The […]
Why bother with Physical Breach Tests?

A physical red team (breach) test is a real-world simulation of a physical breach. Think: tailgating into a secure office, picking locks, planting rogue devices, or accessing server rooms without authorisation. Unlike standard security audits, red teamers think and act like real adversaries – covertly probing for the weakest link in physical security protocols, policies, […]
How We Got Here: A Brief Reflection on Cybersecurity’s Foundations

Computer technology as we know it, has existed for the merest blip of time in human history. In less than 90 years we have gone from valves and punchboards to pushing the boundaries of quantum states in an attempt to achieve computations that would take millions of years to achieve otherwise. We landed people on […]
Abuses of AI

Much like Google and Anthropic, OpenAI have released their latest report on how threat actors are abusing AI for nefarious ends, such as using AI to scale deceptive recruitment efforts, or using AI to develop novel malware. It is no surprise that as AI has become more pervasive, cheap to gain access to, and readily […]
Initial Access Brokers – The Gateway to Ransomware and Supply Chain Attacks

Initial Access Brokers (IABs) are part of the cybercrime-as-a-service ecosystem. They have become the first step in a number of high-profile compromises resulting in ransomware and supply-chain threats. These groups collect, package and sell credentials from a variety of sources for a variety of systems (such as VPN, RDP, SSH, etc), selling them with details […]
Why Not Test in Dev?
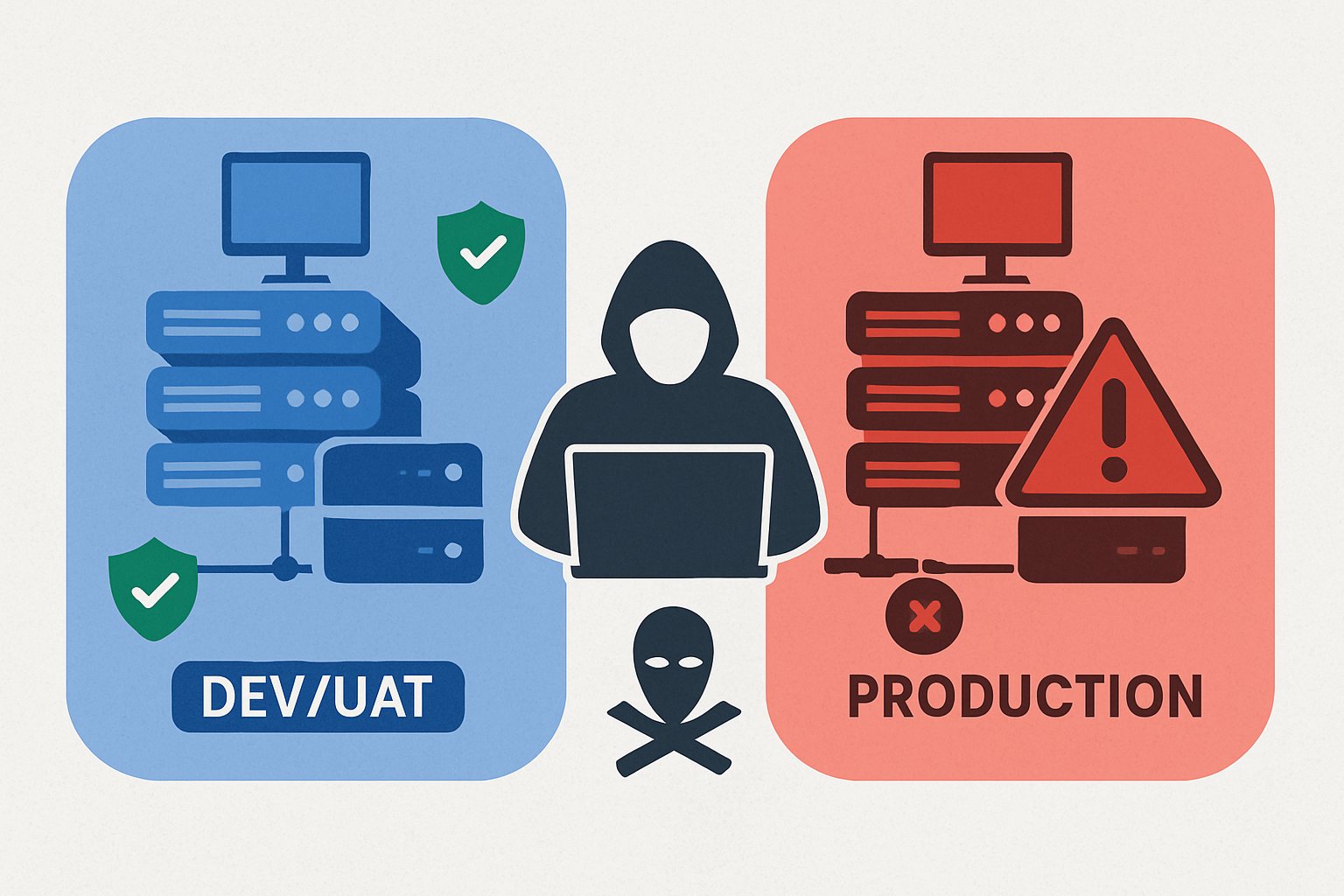
We frequently get asked by clients if we can do our red team tests in their DEV or UAT environments instead of production. We are told its identical to production – same systems, dummy but similar data, same security controls, same user accounts, etc. Etc. We get it, DEV and UAT environments are there to […]
Bait and Switch – Are You Accidentally Recruiting Insider Threats?

Over the last couple of years, we have seen a marked increase in criminal groups infiltrating companies. Either using AI and stolen identities or fronting interviews with disposable candidates all the way through until the contract is signed, and then an alternative person shows up to start the job. In many cases once they have […]
Underinvestment in Cybersecurity

In the last few decades IT systems have become a significant factor for every industry, increasing productivity, improving service offerings and increased the speed at which companies can deliver services. It is only right therefore that we ensure that these systems are not abused, damaged, or misused in a manner which can undermine the organisation […]
The Cost of a Breach

IBM’s 2024 Cost of a Data Breach report, identified that the average cost of a data breach in the UK reached £3.58 million, and that this cost had increased 5% since 2023. Verizon’s 2025 Data Breach Investigation report, suggested there was a 37% increase in ransomware attacks being reported, with a median payout of $115,000 […]